Agentless Threat Protection
Security You May Already Own
Security Has Changed and so is Your Solution
It takes just one malicious outbreak on your network to understand the effectiveness of your security defenses. Preventing an outbreak or breach is important, but even more vital is how do you determine the impact it has had, which systems were compromised, have controls to quickly remediate, and then how to analyze how it happened in the first place.
Organizations have been accustomed to running antivirus and anti-malware solutions for years from a variety of vendors. However, many of these solutions are based on an older type of recognition such as that found in regularly updated definition files. Attack vectors are morphing every day and so should your security design.
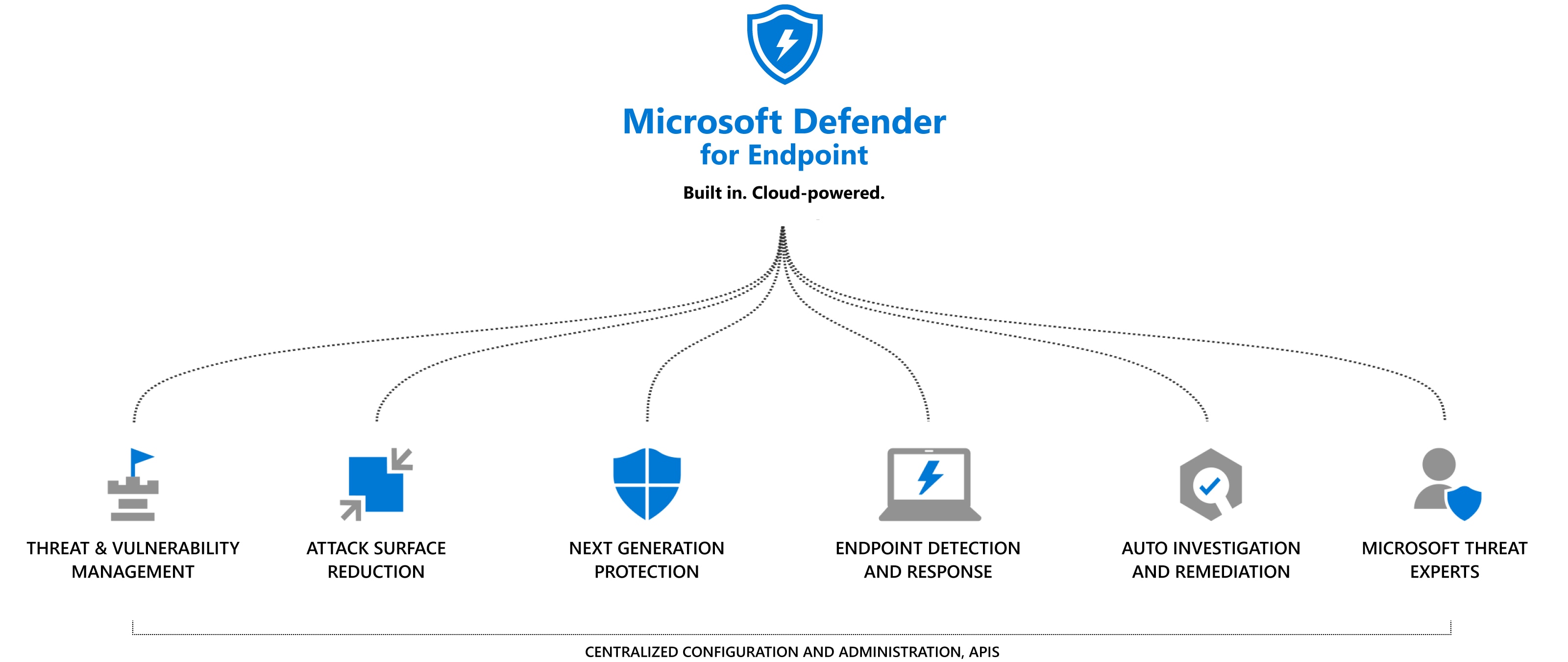
Enhancing Your End Point Security
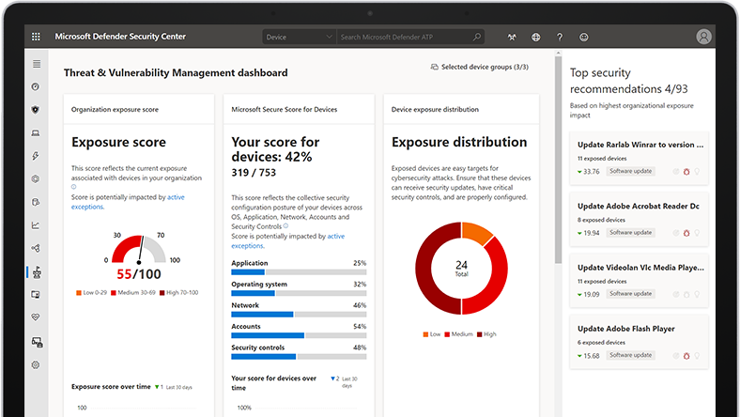
With attack vectors now targeting individual users, it is as important as ever to have a robust endpoint security solution. If you are using Windows 10 or higher, chances are that you already own an industry leading anti-virus/anti-malware solution that is already built into the operating system rather than being installed. And, chances are that you already own the cloud license to enable centralized management and greater capabilities. Windows Defender has grown over the years into a leader in detection and remediation of endpoint malicious activity. Most importantly, using Microsoft Defender for Endpoints, the remediation and research into breach activities are unmatched by any competing products. With a graphical representation, this tool enables security teams to map exactly the point at which an attacker entered your network, how the attacker moved throughout your network and the activities they engaged in. It is one thing to remediate a network breach but having the rich details of exactly how the breach occurred enables us to make sure any vulnerabilities in the network are found and corrected to prevent future breaches.
Use What You Are Paying For – Nothing More
There are several Microsoft 365 subscriptions that enable the advanced and centralized capabilities of Microsoft Defender Advanced Threat Protection. So chances are that you already are paying for this technology while paying for a secondary solution. We will review your current endpoint security solution, evaluate your Microsoft 365 licenses, provide a full cost analysis, and provide an overview of the most advanced endpoint product available.