Locate Threats Before They Become One
What is Shadow IT?
While an organization’s technical department provides the tools needed for productivity, many organizations are now concerned about applications and tools they are not aware of. These applications and tools are seen by users and randomly installed, sometimes going viral before a technical department is aware of its existence. While users consider these new tools to be “cool” and perhaps better than what is provided to them, there are very real dangers to an organization’s data security and potential network breaches. Sanctioned tools or not, the technical department is responsible for all software on the network. The problem becomes, how are these applications detected and stopped?
Installing applications on a network without the knowledge of network administrators is called “Shadow IT.”
Why You Need to be Concerned about Shadow IT
Security of an organizations data is now everyone’s concern. Whether it be an organization’s intellectual property or employee records, the data must be secured. Now imagine if your organization is in the financial or healthcare industry where SOX or HIPPA compliance is mandatory, or you are under the new GDPR regulation.
If an employee downloads a cloud based application that is not compliant with any of these regulations and he/she begins using it with colleagues who also installed it to share sensitive information, your organization is now in breach of these regulations and laws. Data may be sent through these applications in an unencrypted format through a hosted environment in a country known for cyber-crime activity.
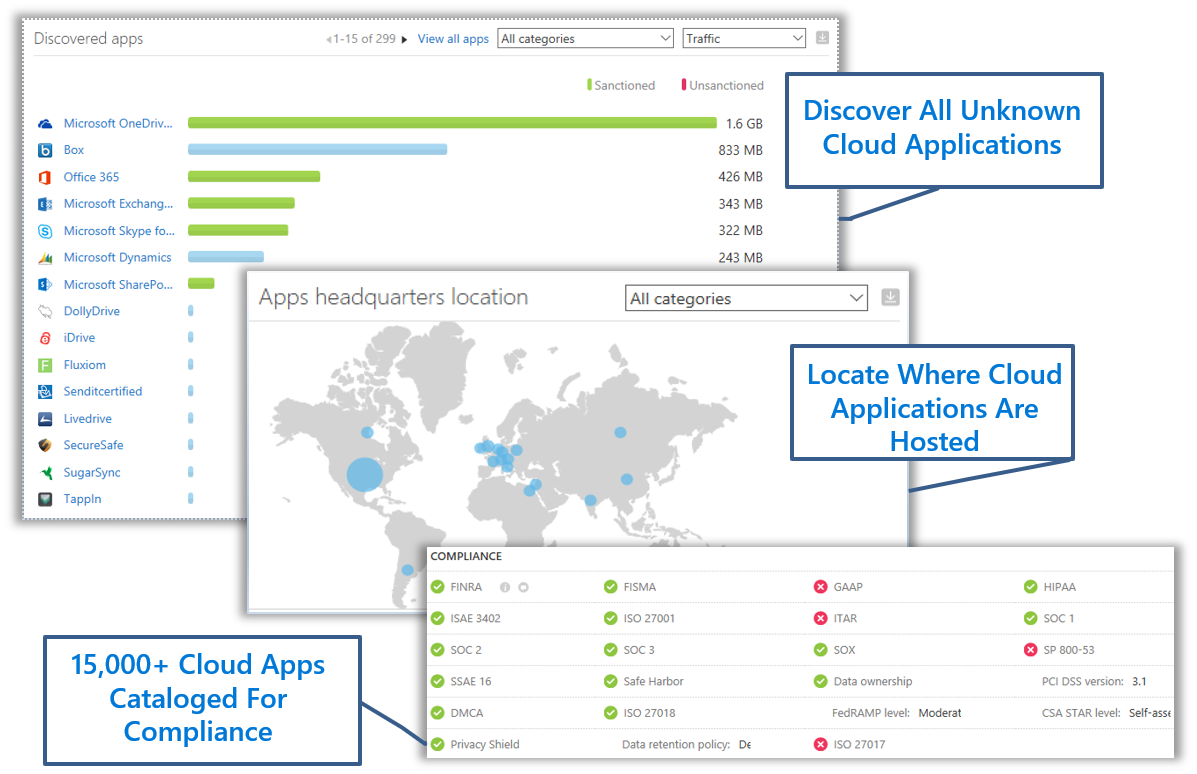
Shadow IT Discovery Assessment
We have the skilled personnel, firewall log scanners and project management expertise to evaluate your overall risk of Shadow IT. We use our uniquely developed methodology in our approach to Shadow IT discovery. Combined with the power of unique capabilities within the Microsoft cloud, we will carefully evaluate your firewall logs to discovery exactly what cloud based applications are being used. We will then present this information back to you at a high level and offer of how we will engage with your users and organization to mitigate the use of these services and educate users on how to use sanctioned services.